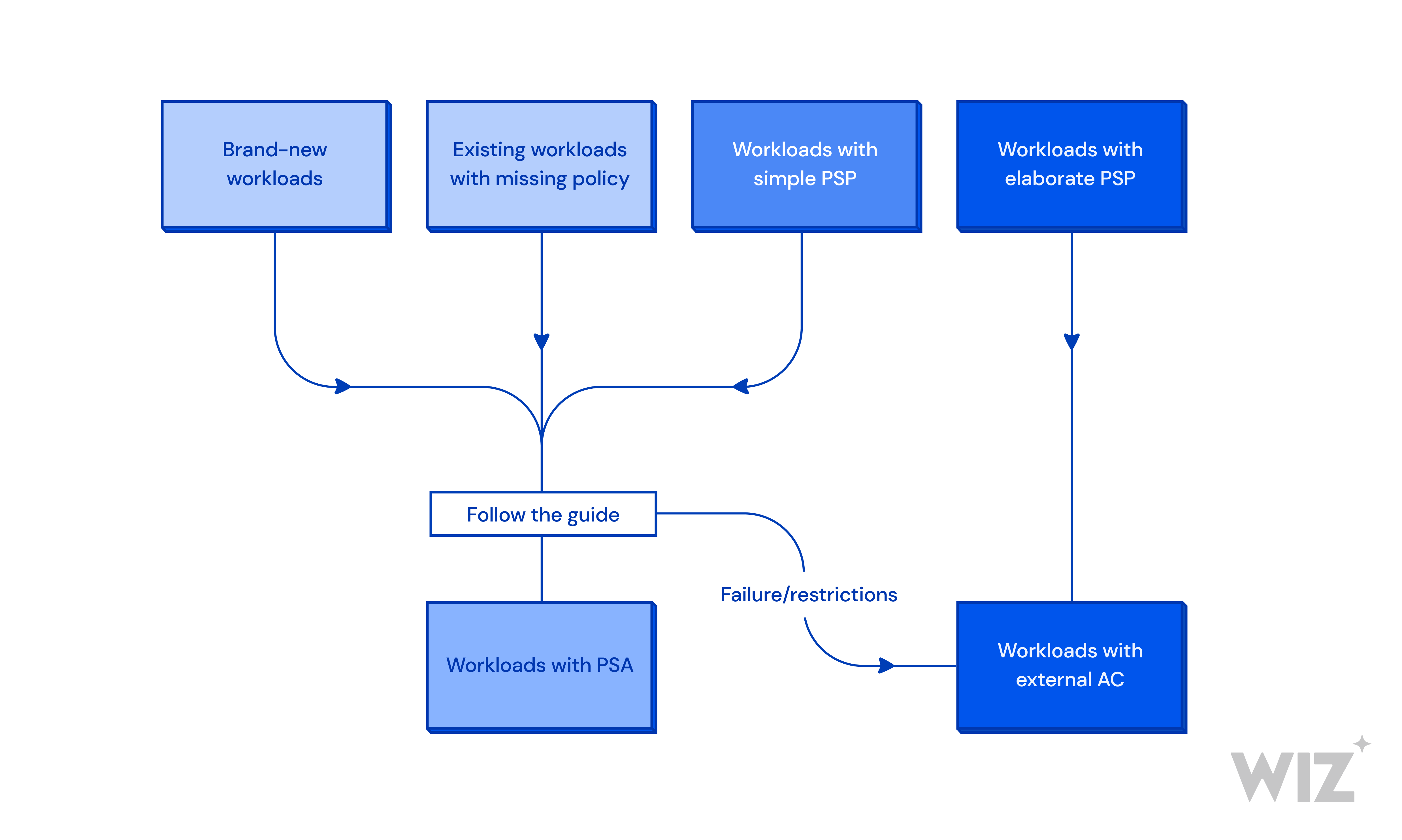
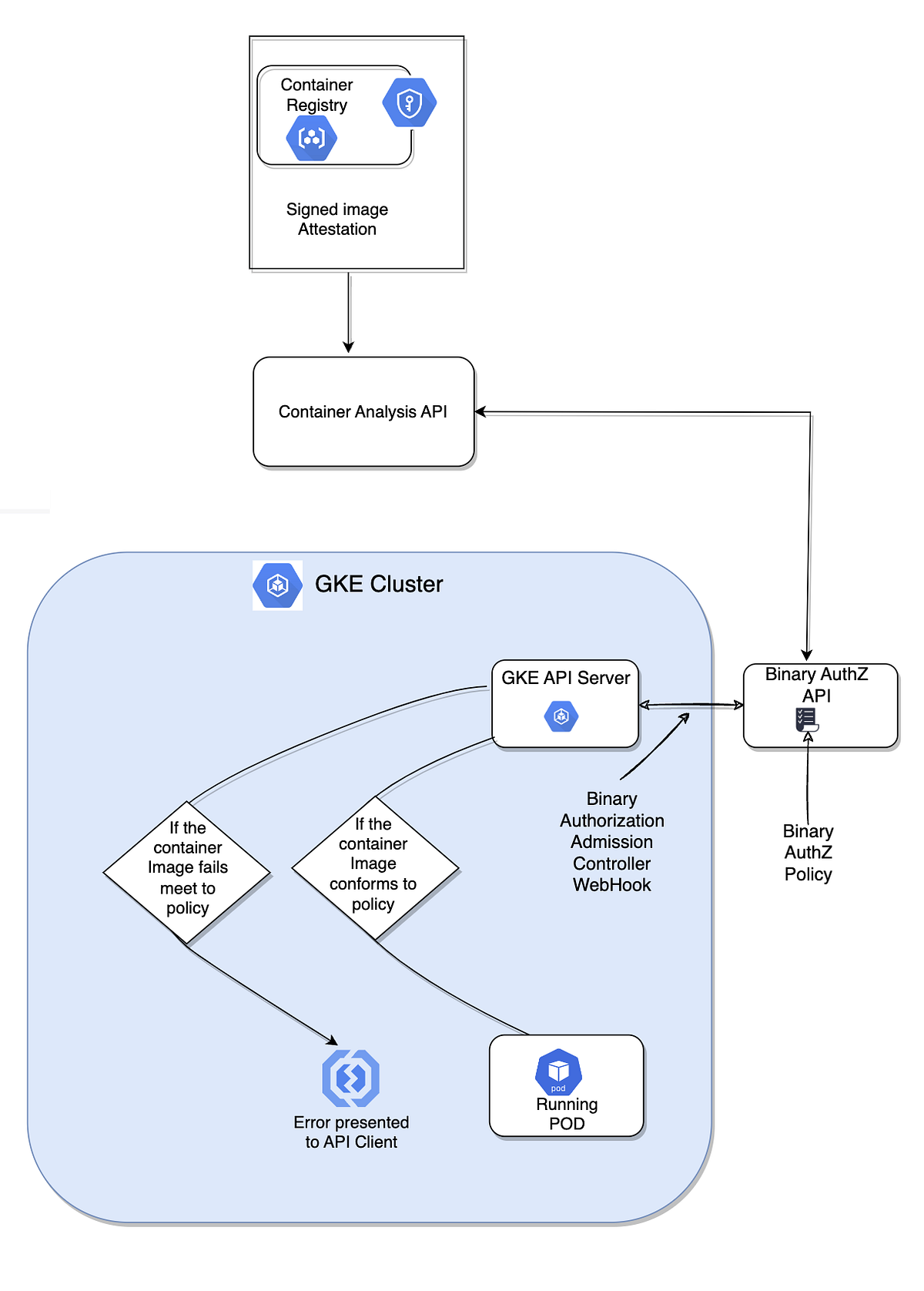
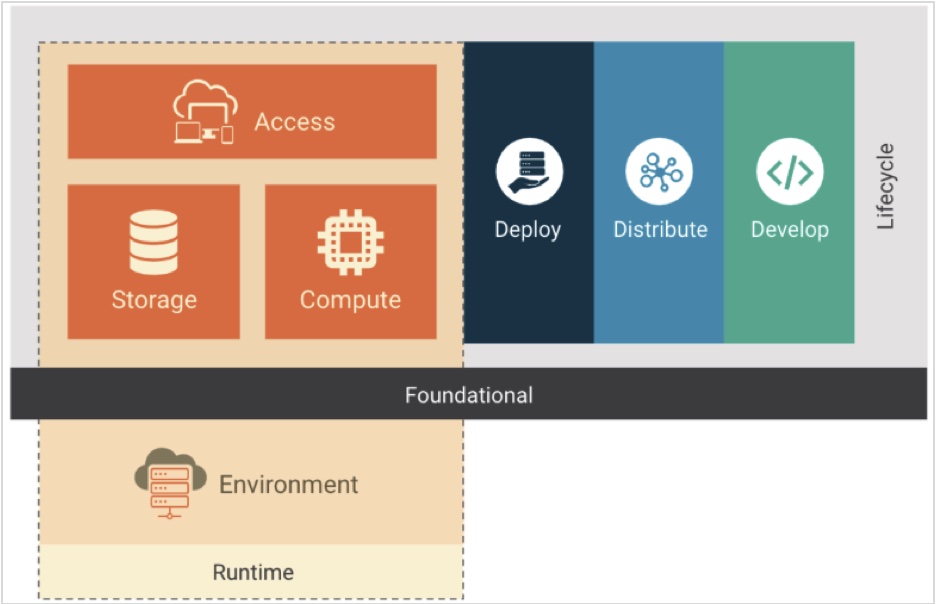
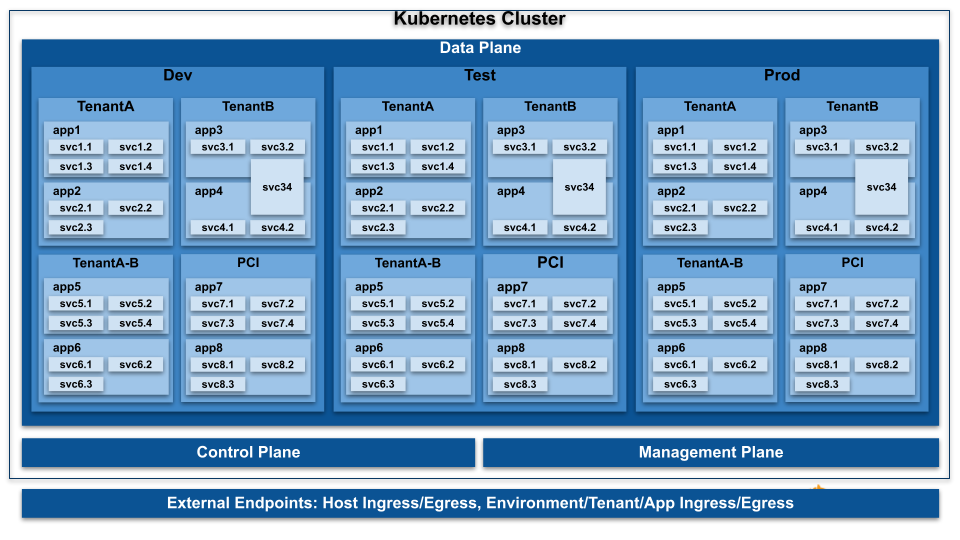
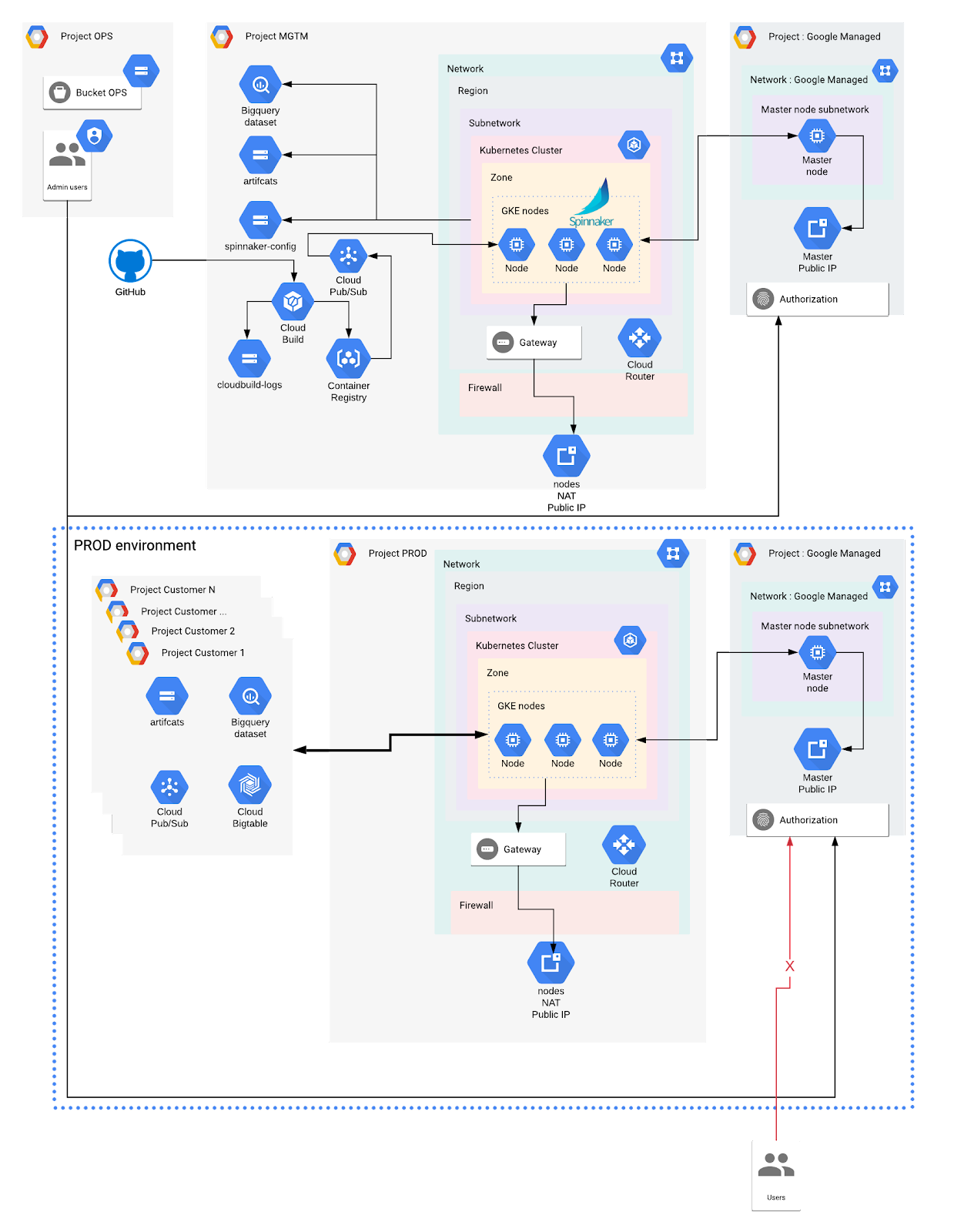
Sécurité kubernetes : Comment réduire votre surface d'attaque grace à GKE : Anthos et policy controller | by Vincent Ledan | Medium
GKE Security Posture Management : Automatic Detection of GKE Security Concerns | by Ankur Gautam | Google Cloud - Community | Medium